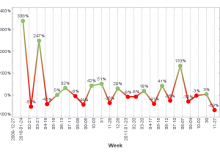
Cybersecurity is a challenging task since data threats keep multiplying and evolving year after year. Unauthorized passwords and permission changes are common means of pursuing access. What steps should enterprises take to track them? Read about them here.