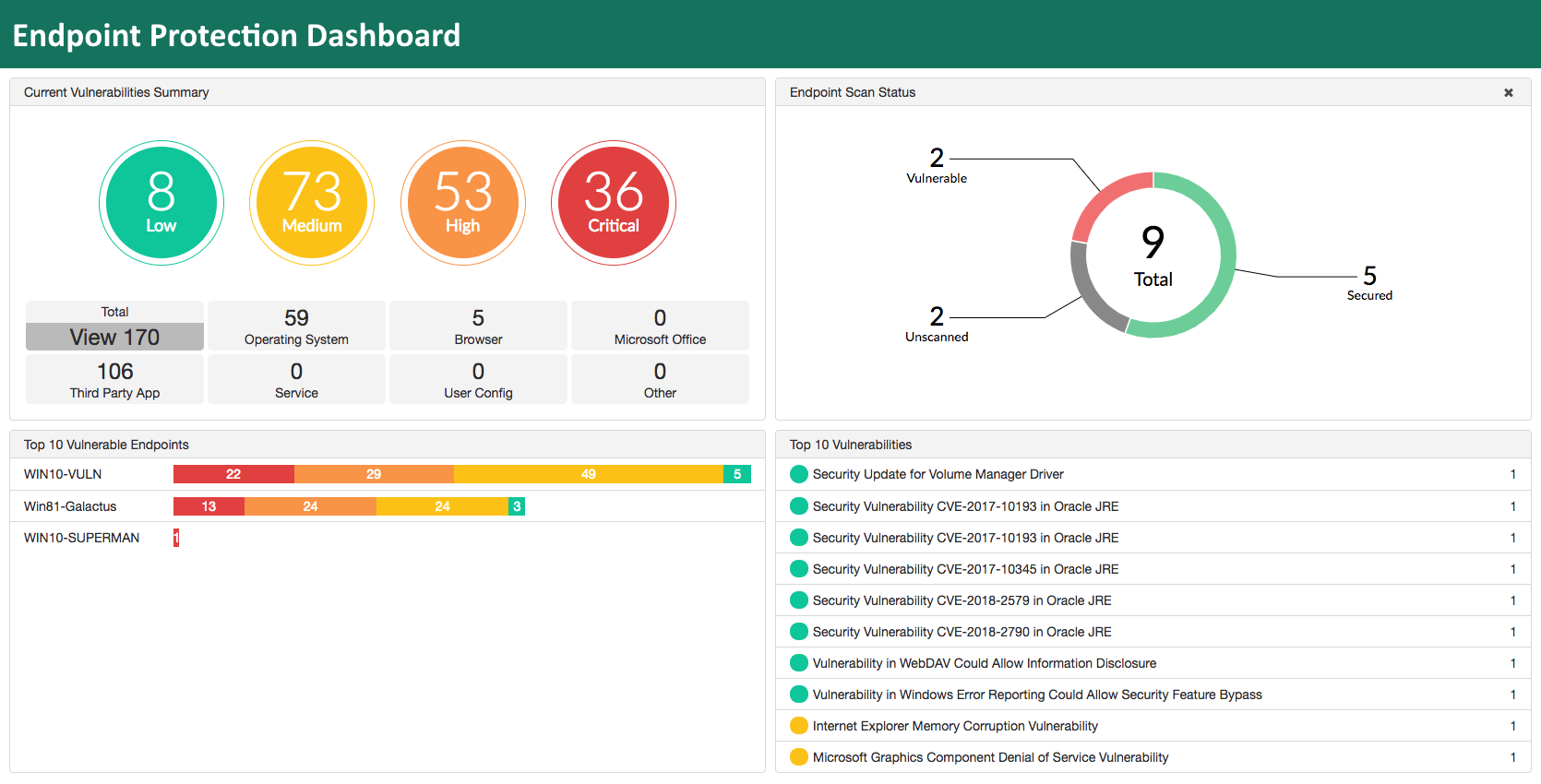
What KPIs and Analytics Are Used on Endpoint Protection Software Dashboards?
One of the first lines of security against a wide range of online attacks is Endpoint Protection Software (EPS). Analytics and Key Performance Indicators (KPIs) are essential for tracking how effective these defenses are being maintained.
This article examines Endpoint Protection Software dashboard KPIs and analytics to help enterprises protect their digital perimeters.
| #1 Ranking: Read how InetSoft was rated #1 for user adoption in G2's user survey-based index | Read More |
Threat Detection and Prevention Rates
KPIs pertaining to threat detection and prevention rates are clearly shown on dashboards for endpoint protection software. These metrics measure how well the program detects and eliminates any dangers before they have a chance to do harm. A high danger detection rate and quick preventative action indicate strong security standards, boosting trust in the software's ability to stop various cyber-attacks.
Real-time Incident Response Metrics
Resolving security events quickly is essential to reducing possible harm. Dashboards for endpoint protection software provide incident response numbers in real time, giving users a better understanding of how quickly the system responds to new threats. Quick reaction times demonstrate how adaptable the software is in managing security events, strengthening an organization's defenses against ever-changing cyberthreats.
Malware Analysis and Classification
One of the most important components of endpoint security is the analysis and categorization of malware. Software dashboards provide key performance indicators (KPIs) for the detection, classification, and further examination of malware. By helping businesses understand the kind of dangers they encounter, these metrics enable them to take preventative action against similar assaults in the future.
Endpoint Compliance Metrics
It is crucial to make sure that every endpoint on a network abides by security regulations. Dashboards for endpoint protection software provide key performance indicators (KPIs) linked to endpoint compliance, giving a general picture of how effectively endpoints conform to set security guidelines. Compliance metrics help firms enforce consistent security procedures on all endpoints and spot any vulnerabilities.
User Activity and Anomaly Detection
Keeping an eye on user behavior is essential for quickly identifying any security breaches. Dashboards for endpoint protection software have KPIs for anomaly detection and user activity. A security concern may be indicated by unusual patterns in user behavior, necessitating a rapid examination and reaction.
System Resource Utilization
The functionality of a system shouldn't be compromised by endpoint protection software. KPIs pertaining to resource use are included in dashboards, guaranteeing that the program runs effectively without placing an excessive burden on endpoint devices. Sustaining strong security protocols and a smooth user experience both depend on optimal resource management.
Patch Management Metrics
There are serious security dangers associated with unpatched vulnerabilities and outdated software. KPIs for patch management are included in endpoint protection software dashboards, which show the status of software updates on all endpoints. Patching systems on time is crucial to improving overall system security and blocking possible entry points for cyberattacks.
Threat Intelligence Integration
Dashboards for endpoint protection software often include threat intelligence-related KPIs. These metrics assess how well the program integrates threat information in real time into its protection systems. A software's total effectiveness is increased by effective integration, which guarantees that it continues to adapt to the most recent cyber threats.
 |
Learn about the top 10 features of embedded business intelligence. |
Incident Investigation and Resolution Times
Following a security event, it is critical to conduct a prompt and comprehensive investigation. Dashboards for endpoint protection software provide key performance indicators (KPIs) for issue investigation and resolution timelines. Rapid resolution reduces the effect of intrusions on organizational assets and is indicative of a proactive security posture.
User Training and Awareness Metrics
Cybersecurity breaches continue to be significantly influenced by human mistake. Dashboards for endpoint protection software provide KPIs for user awareness and training. This set of metrics assesses how well educational initiatives improve users' comprehension of security procedures and lower the probability of unintentional security breaches.
Threat Landscape Analytics
For proactive cybersecurity measures to be implemented, it is essential to comprehend the wider threat picture. Dashboards for endpoint protection software include KPIs for threat landscape analytics, which provide businesses information on the kinds and frequency of threats. Organizations may use this information to keep ahead of new cybersecurity issues and to guide strategic choices.
Compliance with Regulatory Standards
Strict regulatory requirements must be followed by several businesses in order to guarantee data security and privacy. Dashboards for endpoint protection software provide KPIs for regulatory compliance, allowing businesses to monitor and prove that they are adhering to norms and laws that are particular to their sector.
 |
Learn the advantages of InetSoft's small footprint BI platform. |
Behavioral Analysis Metrics
Dashboards for endpoint protection software include KPIs for behavioral analysis, which evaluate system and user activity for anomalies. Behavior anomalies may be a sign of possible security risks, and these metrics help companies identify and take quick action in the event of anomalous behaviors.
Network Traffic Analysis
It's essential to keep an eye on network traffic in order to spot and eliminate such dangers. KPIs for network traffic analysis on dashboards for endpoint protection software provide information about data flow and assist businesses in spotting potentially dangerous activity and security lapses in their networks.
Threat Hunting Effectiveness
Dashboards for endpoint protection software provide KPIs that track how well threat hunting efforts are working. Threat hunting is the proactive process of looking for and locating hidden dangers on a network. This set of metrics evaluates the software's ability to identify and eliminate risks before they become more serious.
Incident Severity and Impact Metrics
Security events are not all the same. Dashboards for endpoint protection software provide KPIs that classify event severity and evaluate the possible effects on the company. Recognizing the seriousness of occurrences aids in resource allocation and response prioritization.
 |
View the gallery of examples of dashboards and visualizations. |
Phishing Detection and Response Rates
Phishing assaults are still a common way for threats to get in. Dashboards for endpoint protection software provide key performance indicators (KPIs) linked to response and detection rates for phishing attempts, providing information on the program's capacity to recognize and block phishing attempts. Robust defense against social engineering attempts is shown by high detection and quick reaction rates.
Endpoint Encryption Status
One essential component of data security is making sure that sensitive data is encrypted on endpoints. KPIs pertaining to endpoint encryption status are shown on dashboards for endpoint protection software, giving a general idea of the percentage of endpoints that are encrypted actively. This measure assists firms in adhering to privacy requirements and maintaining data confidentiality.
Incident Forensics and Analysis
Extensive forensics and analysis are necessary after a security event to determine the source of the attack and improve defenses. Dashboards for endpoint protection software measure the breadth and efficacy of investigations conducted after a security breach using KPIs pertaining to event forensics and analysis.