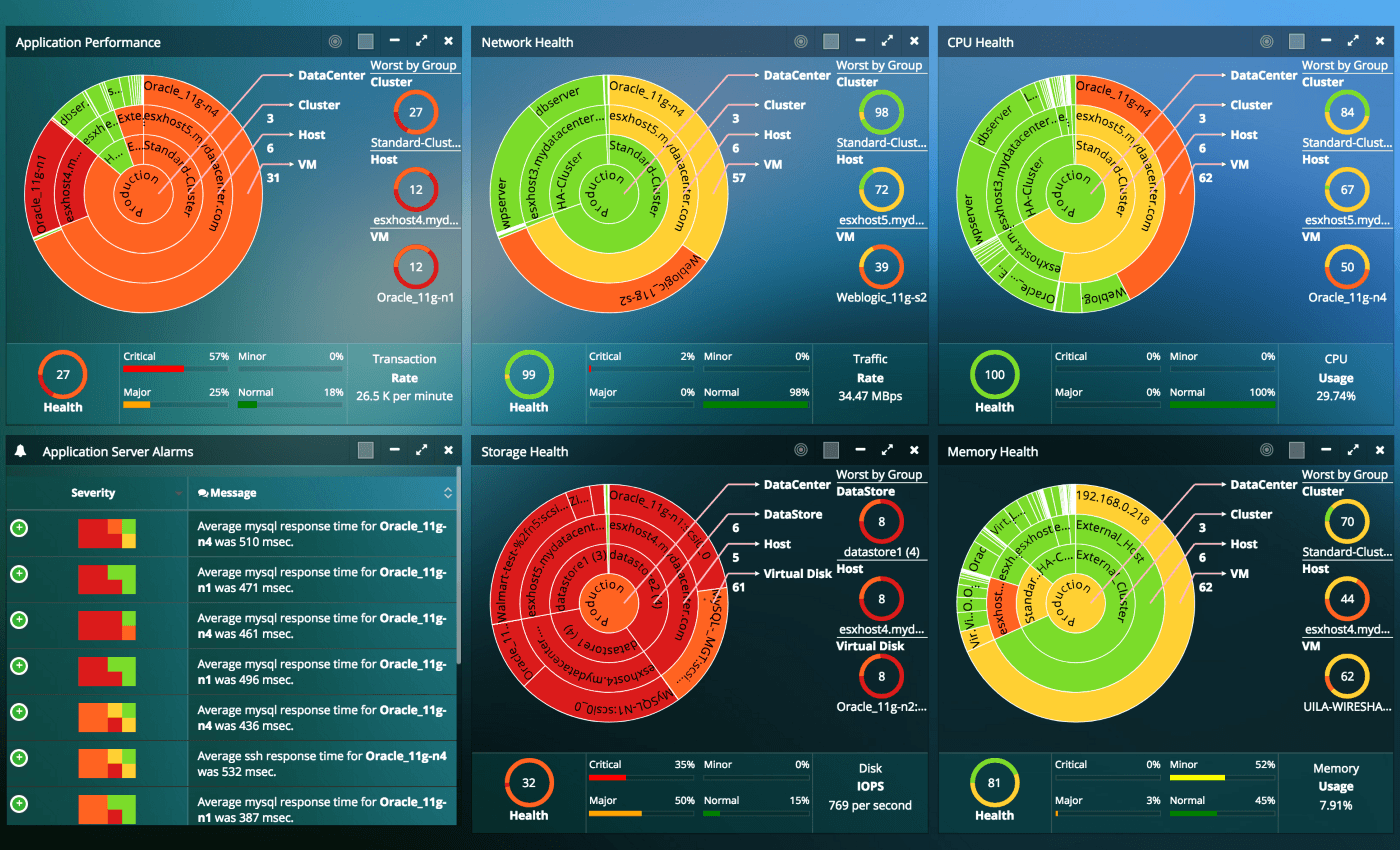
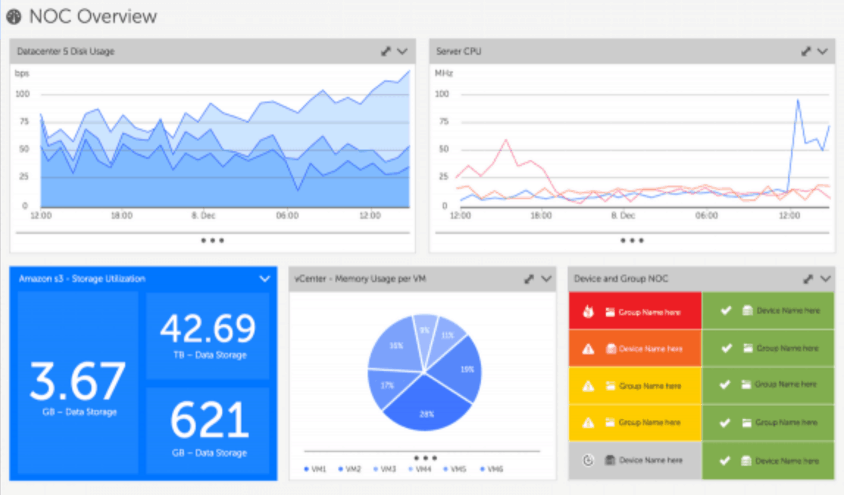
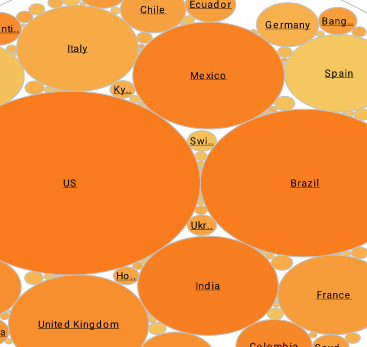
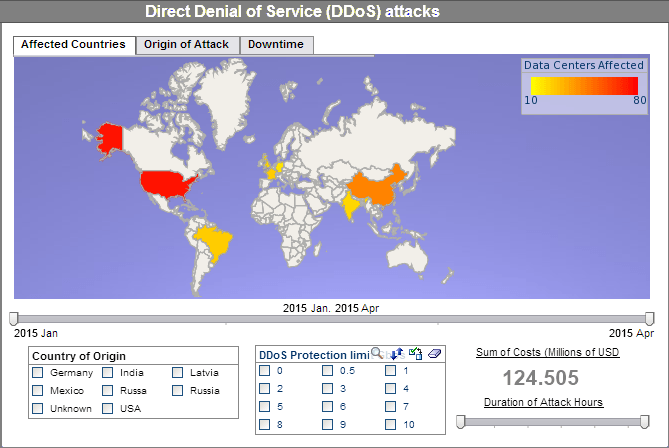
Global Network Intrusions Visualization
The Global Network Intrusions Visualization exhibits the informative and visually pleasing features of InetSoft's business intelligence solution. A pioneer in dashboard, reporting, and data mashup, InetSoft is an innovator in transcending traditional business intelligence with more effective and efficient tools and solutions, providing enhancements in everyday business operations.
With a simple point-and-click environment, the dashboard below allows users to create separate tabs for different charts allowing different perspectives on the intrusion levels of the selected countries.
In addition to the various charts presented, users are empowered with fully customizable filtering and sorting options, like the range sliders, radio buttons, and brushing tool, unique to only InetSoft, for greater control over the search and analysis process. These tools specifically can control the date range, country of origin, and intrusion type.
InetSoft specializes in creating visualization software for organizations of all sizes looking to improve everyday operations and help monitor and create long term objectives in perspective.
| #1 Ranking: Read how InetSoft was rated #1 for user adoption in G2's user survey-based index | Read More |
Capabilities of InetSoft's Data Visualization Application
- Analyze and explore information by using filtering tools
- Create and adjust charts with ease
- Leverage user-driven data mashup
- Upload and sift through multi-dimensional data to spot trends and aberrations
- Slice and dice data with simple point-and-click method
- Reproduce and share visuals
Best Practices for Network Intrusion Detection
- Keep Signature Definitions Updated: Regularly update the signature database to detect the latest threats and vulnerabilities.
- Baseline Network Traffic: Establish a baseline of normal network traffic to more easily identify anomalies or suspicious behavior.
- Use Anomaly Detection: Implement anomaly-based detection to identify unusual network behavior that may not be captured by signature-based detection.
- Segment the Network: Divide the network into segments or zones, and deploy intrusion detection systems (IDS) strategically to monitor traffic within and between segments.
- Monitor High-Value Assets: Focus on monitoring critical systems, servers, and sensitive data repositories where breaches could have the most severe impact.
- Encrypt Sensitive Traffic: Encrypt data in transit using secure protocols like TLS/SSL to protect it from interception.
- Leverage Threat Intelligence: Integrate threat intelligence feeds to enrich data and provide context to detected threats, allowing for better decision-making.
- Utilize Behavior Analysis: Implement behavior-based detection to identify patterns of activity indicative of an attack, such as port scanning or unusual traffic flows.
- Monitor Outbound Traffic: Don't just focus on inbound traffic; monitor outbound traffic as well to detect any attempts to exfiltrate data.
- Implement User and Entity Behavior Analytics (UEBA): Analyze the behavior of users and entities to identify any unusual or suspicious activity.
- Set Realistic Alerts and Thresholds: Fine-tune alerting thresholds to reduce false positives and ensure that alerts are actionable.
- Integrate with Security Information and Event Management (SIEM): Integrate IDS with a SIEM system to correlate and analyze data from various sources for a more comprehensive view of the security landscape.
- Regularly Review and Analyze Logs: Perform routine reviews of IDS logs to identify trends, patterns, and potential threats.
- Conduct Regular Penetration Testing: Test the effectiveness of the intrusion detection system by simulating attacks to identify any blind spots or weaknesses.
- Automate Response and Remediation: Implement automated response mechanisms to quickly address detected threats, such as blocking malicious traffic or isolating affected systems.
- Stay Informed and Educated: Keep abreast of the latest cybersecurity threats, vulnerabilities, and best practices to adapt and evolve your intrusion detection strategy.
InetSoft's BI application makes a good choice because it's:
Easy
- Enjoy a rapid implementation; minimum specialized IT expertise required
- Experience a shallow learning curve for business users; only Excel-level skills needed
- Make it easy for analysts & administrators; no SQL experience required
- Scale up with zero-client deployment and no per-user licensing
Agile
- Provide maximum self-service through ad hoc and visualization analysis
- Enable self-service also at data level: end-user defined data mashup
- Accommodate quick, formal, and experimental changes
Robust
- Address advanced and mass needs
- Run on a high performance, secure infrastructure
 |
Read the top 10 reasons for selecting InetSoft as your BI partner. |
More Articles Related to Network Dashboards
Configuring iFrame Attributes - You may alter the behavior and look of iFrames by using their many features and settings. When setting up your iFrame, you may utilize the following common attributes: sandbox: Security is provided via the sandbox property, which limits the capabilities of the embedded content. Which operations, such as navigating, submitting forms, and executing scripts, are permitted may be specified...
Demand Paging Problem - The response time of a reporting system needs to be reduced as much as possible even when the reports that the reporting server is producing are very large. A report server's response time is measured by recording the time difference between the initial request for a report and when the first page is returned to the end-user. Most other reporting tools retrieve...
Information about InetSoft's Software for Dashboarding - Read information about InetSoft's easy and agile dashboard analysis software. We run an automated program that cleans all the computers and makes sure that as students move into our campus housing that their computers has anti-virus software installed...
Messaging Network KPIs: Message Delivery Success Rate - One of the most basic KPIs for mobile carrier messaging networks is the message delivery success rate. It calculates the proportion of communications that reach their intended recipients successfully. This KPI is crucial for evaluating the messaging service's overall dependability. A network's efficiency may be determined by its success rate; on the other hand, a low success rate might...
Network Analyst KPIs: Network Error Rate - The proportion of data packets that are damaged or lost during transmission is known as the network error rate. This KPI is used by network analysts to identify problem areas and resolve them. Poor data integrity and performance might result from high network error rates...
Share Reports Via Social Media - You can easily export reports as PDF files so that they can be viewed offline. This makes it easier to view the report when no internet connection in available. PDF files can be generated on an as-needed basis from the report toolbar using the Export or Email features, or can be automatically created and distributed by a scheduled task. PDF files can also be created by the built-in...